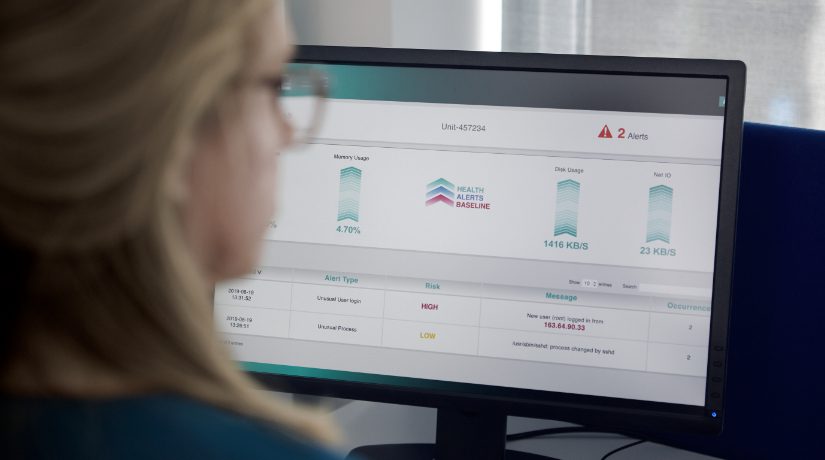
In this article, Icomera’s award-winning Business Continuity consultant Mark Hoffman and cybersecurity engineer Chris Baker outline a number of security best practices which operators should follow when it comes to (i) designing and building resilient onboard networks and (ii) ensuring the most effective response to any attack.
Cybercrime continues to rise[1] and has been classified as the biggest threat businesses face today[2]. It is little wonder that new laws are being proposed and passed in the EU[3], UK[4], and US[5] which will push organisations to further strengthen their resiliency.
This upward trend is clearly disconcerting, and transport operators must continue to deploy new detection and response tools in order to establish robust protection systems. However, these tools are simply one element in the overall arsenal of cyber-defences that organisations should rely on. There are also a range of frameworks, processes and methodologies that should be incorporated into a company’s security planning which are fundamental in helping ensure that they are well protected and prepared.
Secure by Design
The transport industry’s move towards digitalisation offers significant advantages in terms of simplifying network architecture and facilitating communication between different onboard components. However, greater connectivity can also increase the number of potential entry points that can be targeted in a cyber-attack. Without the right design in place, a single vulnerability in one system can be exploited to put other networked systems at risk. Similarly, the fact that more and more systems can be accessed remotely brings new challenges that must be considered.
This is why it’s imperative that security is prioritised right from the outset when planning an onboard network, rather than as an additional consideration to be investigated down the line. Indeed, one simply cannot think of digitalising the components on a vehicle, without keeping security front of mind from the initial design phase.
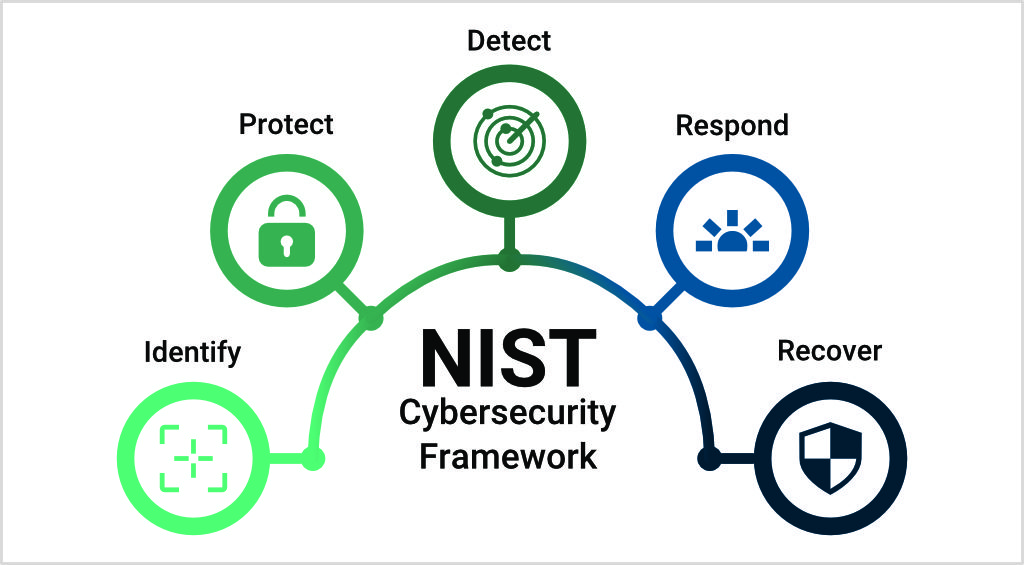
The system architecture must be designed in a way which effectively deters and prevents against breaches, following best practice standards in line with established protocols such as ISO 270016, IEC 62443[7], and the National Institute of Standards and Technology (NIST) framework for cybersecurity[8].
As the NIST framework outlines, the starting point in a robust cybersecurity approach involves being able to identify and protect against threats; these are key to then being ready to detect, respond and recover from an attack appropriately.
Designing and Maintaining an Onboard Network: Key Security Considerations
- System Architecture Design – It is common for legacy onboard systems to connect to one another over a flat network with no segmentation. The problem with this approach is that penetration in one area of the network can result in access throughout the system. The use of network segmentation isolates any penetration to a single area, significantly reducing the overall exposure and risk.
- Access Control and Monitoring – Intelligently managing and monitoring access to a network helps ensure that only those that require access can gain entry. Access can be controlled by means including establishing a robust password policy, allowing access only to authorised devices, and implementing automatic account lockouts after multiple unsuccessful login attempts. Additionally, change logs should be actively monitored to verify that no potentially malicious updates are made to the system.
- Continuous Improvement – An effective security approach must acknowledge that protection is an ongoing and evolving process. No-one can afford to become complacent in thinking that a system is ever fully protected; a defensive measure which was robust at the initial design phase may not be tomorrow. Regular penetration tests should be carried out to discover and react to any potential new / existing vulnerabilities, and multi-layered lines of defence should be deployed to help form the strongest possible protective web around a network.
Responding Effectively to a Cyber-Attack
Unfortunately, even with an optimal system architecture design, and with the best possible detection / defence processes and tools in place, transport operators will still be susceptible to a breach at some point, and they must be ready to respond quickly and appropriately when one occurs.
It should go without saying that an organisation’s IT department will play an integral role in any response playbook; technical experts will need to carry out forensics, work to contain and eradicate the threat, and take steps to get systems back online as soon as possible.
However, there is an equally important parallel work-stream that often gets overlooked, and this involves establishing a robust crisis management response. This component involves many other stakeholders within a company and relies on good planning across a range of different departmental areas…
- Business Impact Planning – Before any attack occurs, a detailed assessment should be carried out into which systems are used by the company, what role these different systems play, which departments rely on these systems, and what the business impact would be if a system were to be taken offline. From this analysis, it will be possible to form a clearer understanding of where a security breach would incur the least / most damage, and for the crisis management team to gauge an appropriate level of response.
- Insurance and Legal Planning – Operators cannot afford to wait until an attack occurs to determine their cyber-insurance coverage. They should research the scope and limitations of their policy, as well as confirming the process for how they must engage with a breach coach during a crisis. Additionally, it’s essential to pay attention to legal considerations, ascertaining ahead of time what must be done to meet any obligations, especially when it comes to privacy-related matters (e.g. in the event of a data breach).
- Crisis Decision Planning – When a cyber-attack happens, some extremely tough decisions will need to be made under considerable time pressure. Thankfully, it’s possible to plan ahead. Conversations can take place between relevant stakeholders based on possible attack scenarios, and default positions can be built into an organisation’s incident response plan. These default positions must be based on an operator’s core values and principles, and its appetite for dealing with risk. However, companies must also be willing to deviate from this default based on likely accentuating circumstances; for example, stakeholders can discuss together whether they would be more or less likely to pay a ransom demand in a live incident if the ransom were extremely low, or in a case where there was the additional threat of data exposure.
- Crisis Communication Planning – One of the most important aspects of a cybersecurity response will be in working to protect an organisation’s reputation, and effective communication is key to securing this aim. Again, it’s possible to anticipate and prepare on this front. Based on likely attack scenarios, choices can be taken in advance on what internal / external communications would need to be published. Pre-drafted templates can be created which form the foundation for what these communications might state, allowing teams opportunity for internal discussion on the tonality and messaging, and helping ease pressure when it comes time to deal with a live incident itself.
The bottom line here is that operators who rely solely on their technical IT teams to deal with an attack are only considering half the equation when it comes to security. Without the right crisis management planning, it’s impossible to properly understand what the business impact of any breach would be, and therefore also impossible to make good decisions around how to deal most effectively with it.
In contrast, with the right preparation in place, teams will be far better placed to make good business decisions during a cyber-attack, leading to a far higher likelihood of them gaining the best possible result for the organisation.
Importantly, a well-formed crisis management plan is not only an expectation that operators should place on themselves; it should also be a requirement they place on each of their partners and suppliers.
This article features in Icomera’s 48-page industry report “The Connected Journey Through Transport’s Transformative Decade”.
Supported by data and insights gathered from transport authorities, operators, and technology companies around the world, the report covers the trends and challenges shaping the future of passenger transport, and the role that connectivity will play in achieving the industry’s overarching goals…