Preparing for the cyber threats of tomorrow requires deliberate action by passenger (and freight) railroads to improve the resiliency of assets.
On October 18, 2022, the US Transportation Security Administration (TSA) issued Security Directive 1580-21-01A, intended to make the nation’s’ railroads more secure and resilient to cyber threats by implementing measures aimed at identifying and resolving network and/or system vulnerabilities.
I recently had the opportunity to address the Commuter Rail Coalition at their inaugural summit, informing other industry leaders on the state of safety and cybersecurity best practices.
The reality of the industry remains that most existing, onboard and network-based technologies are antiquated and not designed with security in mind. Disparate operating systems, poor authentication protocols, and manual port-based updates are a handful of the vulnerabilities operators face in managing their video surveillance, passenger information, and other mission-critical systems.
Bruce Cardon, Commuter Rail General Manager of Utah Transit Authority said “All industries need to take the risks of cyber security seriously to avoid or minimize significant cost and disruption. The Commuter Rail Coalition helped bring attention to this priority to leaders in its inaugural Summit. Being attacked is no longer considered an “if” but “when” so leaders need to prepare their organizations both to prevent intrusion and be ready to respond in the unfortunate situation where an attack is successful.
“As industries, like commuter rail, take cyber security seriously and learn from each other, the incentive for bad actors to target them is diminished and the investment will successfully create a shield of protection and deflect attention to reduce the likelihood of attacks.”

As the industry moves towards digitalization, it is imperative that cybersecurity serves as a fundamental aspect of the design. Without the right design in place, a single vulnerability can be exploited to put other systems – and passengers – at risk.
Mitigating these risks requires operators to be ready to detect, respond, and recover from a cyber-attack appropriately.
With the US Department for Homeland Security about to publish a second cyber directive for rail, the industry must do more to protect against and prevent cyber-attacks starting with the actions identified in the Security Directive, including:
-
- Designating a cybersecurity coordinator
- Reporting cybersecurity incidents to the Cybersecurity and Infrastructure Security Agency (CISA) within 24 hours
- Developing and implementing a cybersecurity incident response plan
- Completing a cybersecurity vulnerability assessment to identify potential gaps
Mitigating the Risk of Cyber Threats is a Continuous and Evolving Process
As the supplier and network manager of the underlying communications infrastructure for transportation systems, we are aware of our role and responsibilities in mitigating exposure to threats and vulnerabilities.
Icomera has achieved ISO 27001 certification for information security management. ISO 27001 is a process-based, risk-driven approach focusing on continuous improvement. By putting in place controls according to ISO 27001 – aligned with the NIST Cybersecurity Framework – we understand what assets must be protected against which risks, and how those risks are mitigated.
Additionally, Icomera’s Operations Centre provides round-the-clock support for our clients, ensuring any developing incidents are identified quickly and relevant parties are alerted, and engaged in the response plan at the earliest opportunity.
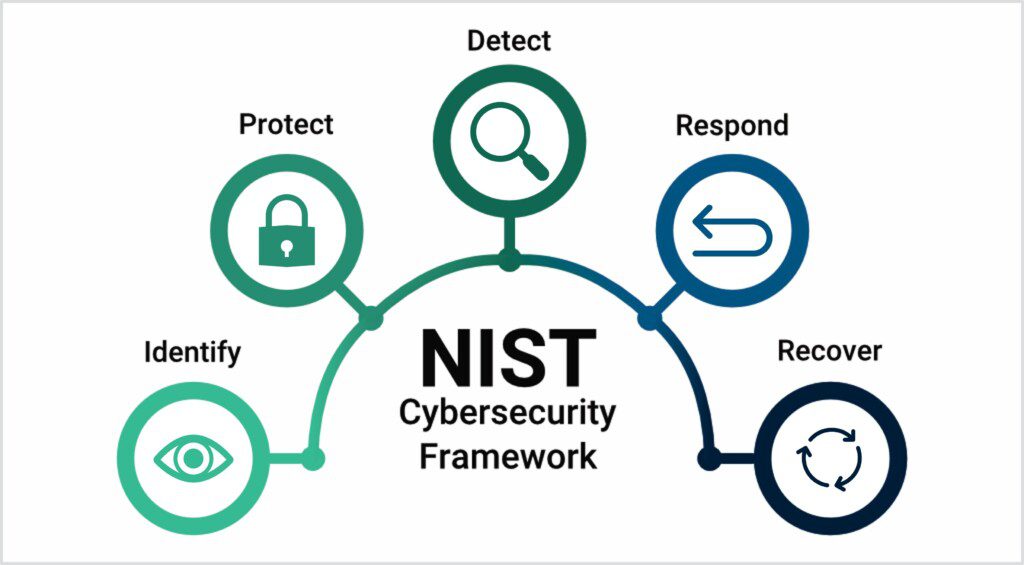
By implementing the right cyber risk management plan, transport operators will be able to identify and protect against threats, and ready themselves to detect, respond and recover from an incident appropriately.
We advise operators to:
-
-
- Incorporate defense and risk mitigation into resilience planning.
- Include suppliers as a stakeholder in their risk assessment.
- Keep the risk register active with interdepartmental involvement.
- Implement a react-emergency shut-off plan.
- Maintain a current cyber framework and process.
-
With an increase in cyber threats towards rail operators and systems, it is evident that a cyber resilience plan will continue to play a vital role in maintaining the viability of services. Operators must contend with – and address – the threats of tomorrow, today.


